New Delhi: Scammers are targeting banking customers in India with a new type of phishing attack by impersonating internet banking portals, the country’s cybersecurity agency has warned. Indian Computer Emergency Response Team, or CERT-In, issued an advisory Tuesday, saying the scammers are hosting phishing websites on the ngrok platform to collect sensitive information like internet banking credentials, mobile numbers and One Time Password (OTP).
"It has been observed that Indian banking customers are being targeted by a new type of phishing attack using ngrok platform," the CERT-In advisory said.
"The malicious actors have abused the ngrok platform to host phishing websites impersonating internet banking portals of Indian banks," it added.
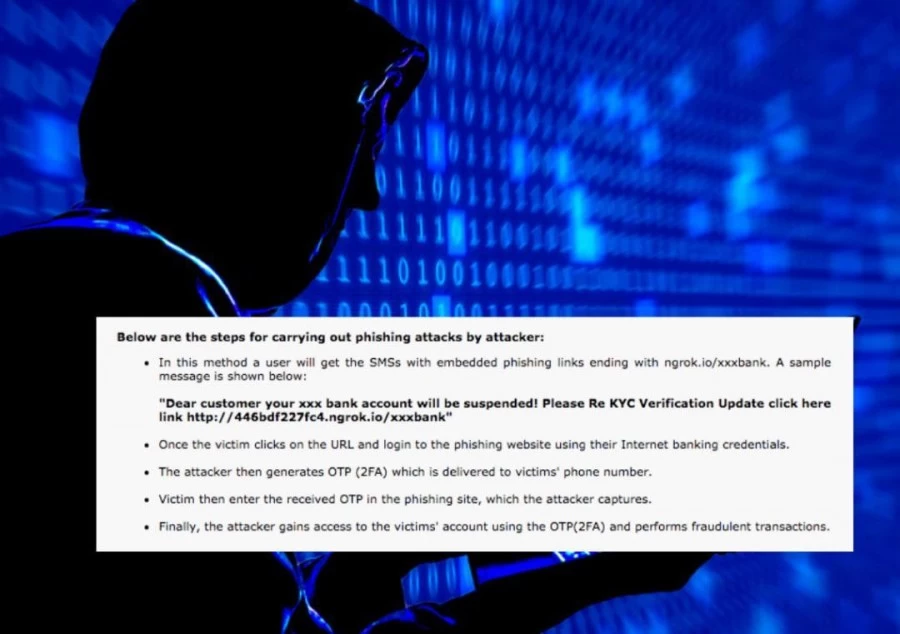
Using a sample SMS, the cybersecurity agency elaborated how the “malicious actors” are tricking banking customers into clicking on phishing websites to carry out fraudulent transactions. The scammers send an SMS with embedded phishing links ending with ngrok.io/xxxbank, where xxx denotes the name of the bank.
“Dear customer your xxx bank account will be suspended! Please Re KYC Verification Update click here link http://446bdf227fc4.ngrok.io/xxxbank,” the sample SMS reads.
CERT-In said that once the customer clicks on the URL and login to the phishing website using their internet banking credentials, the attacker generates OTP using the information. The phishing victim then enters the OTP on the phishing site, which the attacker captures and gains access to the victim's account to carry out fraudulent transactions.
"Phishing websites and suspicious messages should be reported to the CERT-In at [email protected] and respective banks with the relevant details for taking further appropriate actions," the advisory said.
Here are some of the “best practices" listed by CERT-In to prevent such attacks:
Banking customers should look for suspicious numbers that don't look like real mobile phone numbers as attackers often mask their identity by using email-to-text services to avoid revealing their actual phone number.
Genuine SMSes received from banks usually contain sender id (consisting of bank's short name) instead of a phone number in the sender information field.
They should only click on URLs that clearly indicate the website domain.
They can search for the organisation's website directly using search engines to ensure that the websites they visited are legitimate.
Users should exercise particular caution towards shortened URLs, such as those involving bit.ly and TinyURL.